
Securing Webviews
&
The Story Behind CVE-2021–21136
Imdad | Shiv
TRACK 2
Security Engineer,
Grab
Senior Associate,
JP Morgan Chase
The techniques to secure Webviews and the journey on CVE-2021–21136

Any opinions or personal views expressed belongs to us and
not to our employer
3
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

Table of Contents
1. Introduction to CVE and
Webview
2. Journey on CVE-2021-201136
3. In-depth Analysis
4. Common Webview Security
Issues
5. Learnings & Recommendations
4
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

5
Introduction to
CVE and
Webview
6
Common Vulnerability Exposure
CVE, short for Common Vulnerabilities
and Exposures, is a list of publicly
disclosed computer security flaws.
When someone refers to a CVE, they
mean a security flaw that's been
assigned a CVE ID number.
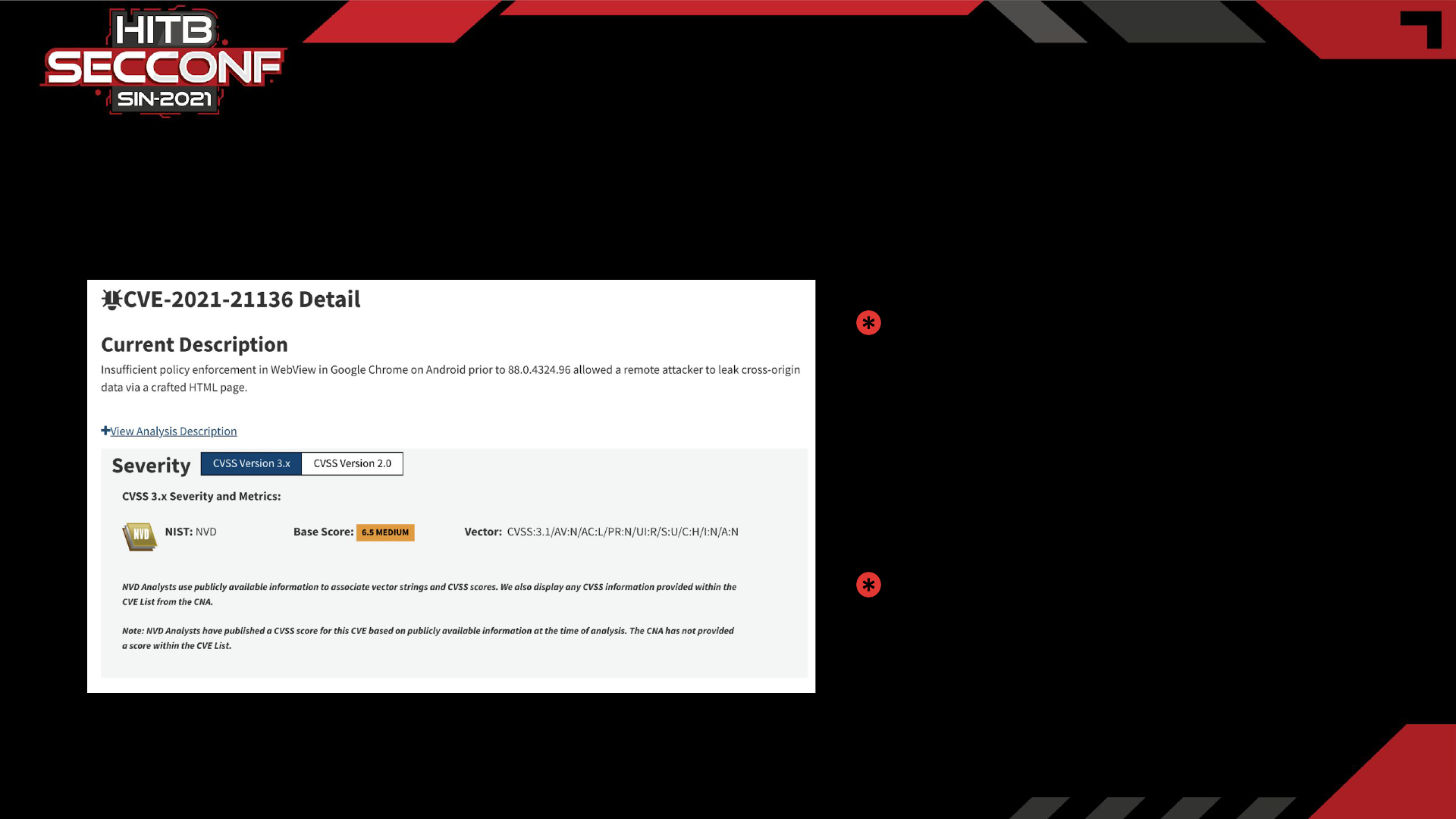
Hello World!
CVE-2021-21136
During security research we found that a
mobile application is leaking sensitive data
in headers to a third-party. This kickstarted
the research behind identifying a security
issue in Android Chromium webview
leading to leakage of auth tokens to
third-parties.
Let’s know what is a CVE and understand the high level details of CVE-2021-21136
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

7
Introduction to Webview
Dedicated web browser instance of an application allows
to display web content directly in the application
Webviews are used extensively currently in the polyglot
architectures
Webview and its applications in modern mobile application development
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

8
Loading Web Content
Loading web content in webview(Normal Load)
We can load the web content using Webview#loadUrl method as shown below:
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

9
Loading Web Content
Loading web content in webview(Authenticated Load)
Android also provides an overloaded version of Webview#loadUrl method which lets us pass
additional request headers such as auth headers to the request as shown below:
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

10
Deeplinks
An introduction to deeplinks and how an improved user experience through deeplinks could
affect security if implemented insecurely
Deep links are specific URIs(Uniform Resource Identifiers)
that are handled by our application to improve the user
experience
For example, fb://profile/33138223345 is a deep link, the
URI contains all the information needed to launch directly
into a particular location within the Facebook mobile app,
in this case, the profile with id ‘33138223345’
Talk Title | Speaker Name here. Can change this on footer menu

11
Journey on
CVE-2021-201136
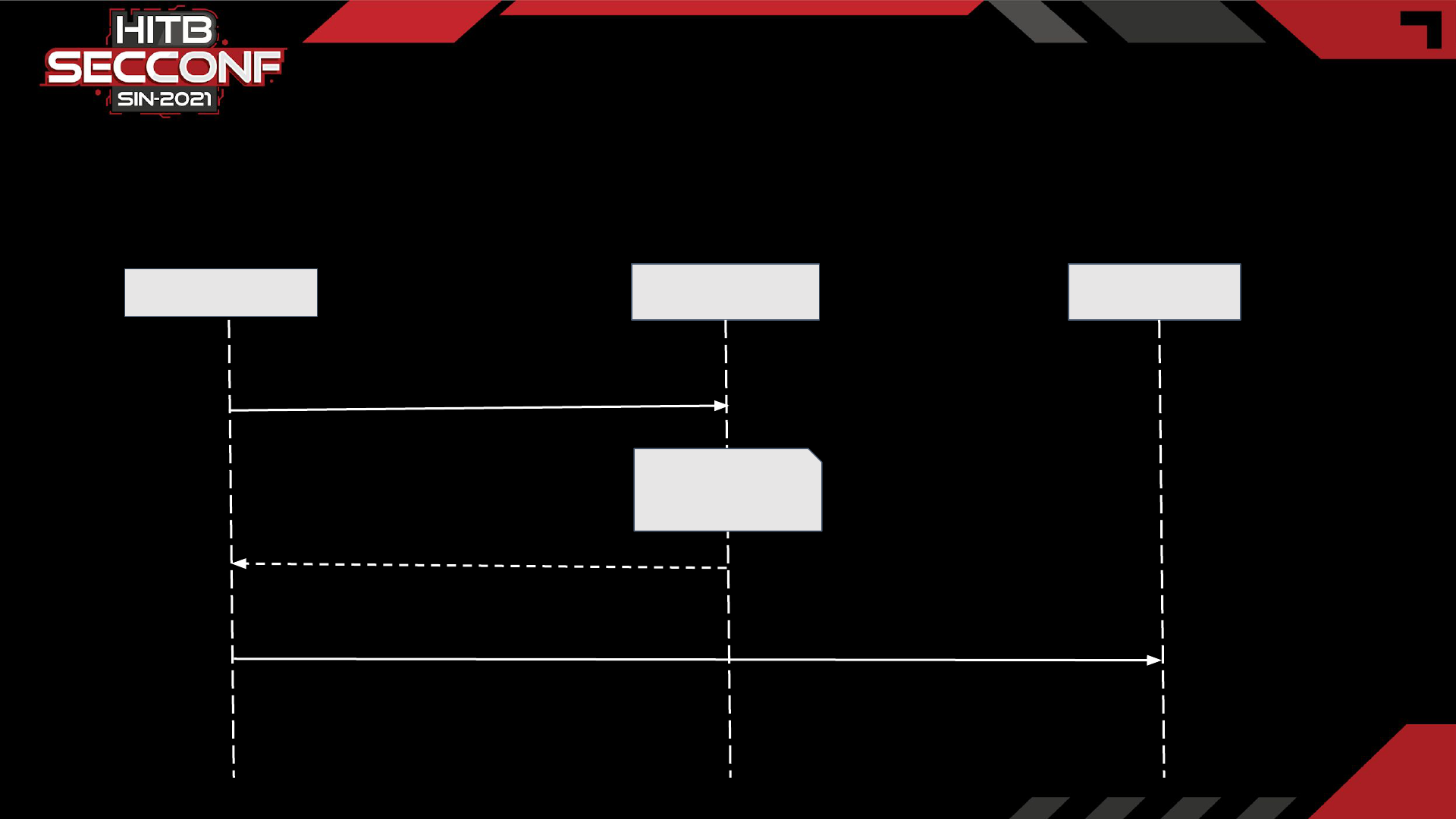
oAuth Use Case
12
GET
/oauth/config?client_id=<client_id>&r
edirect_url=<third-party_url>
Identity Service
Mobile Application
Third-Party
Service
Auth Token sent in header
Verify Auth token and
generates id_token
for the third-party
Redirect to <third-party_url> along with id_token
returns id_token
Understanding oAuth flow in mobile applications
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

The Bug
13
GET
/oauth2/config?client_id=<client_id>
&redirect_url=<third_party_url>
Identity Service
Mobile Application
Third Party Service
Auth Token sent in header
Verify Auth token and
generate id_token for
the third-party
Redirect to <third_party_url> along with id_token
User’s Auth Token exposed to
Third-party
returns id_token
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

14
Initial Observation
The story behind leakage of auth tokens to third-parties!
During our security research we observed that in Android webviews if a
webpage is loaded with some additional headers
using loadUrl(String url, Map<String,
String>additionalHttpHeaders)then it sends the additional
headers to any other requests triggered in the process of loading the URL
such as redirects.
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

15
Timeline
The Journey on Chromium CVE 2021-21136
A
Initiated the analysis with suspected zero day
in Android webviews & reported to Google
Initial observation
Suspected issue in Chromium
August, 2019 December, 2019
Deep Down Investigation
January, 2020
It seems intended behavior and
would need more time for thorough
analysis
Response from Google
February, 2020
Google Accepted
Need more time to fix.
Compatibility issue
November, 2020
Official Fix Released
in Chromium 88
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

16
In-depth Analysis

17
Frontend : Android app
I want DEMO!
An Android webview component. The component loads the webpage with
additional header (Authorization)
Reference: https://github.com/shivsahni/OhMyInsecureWebview
String URL = extras.getString("URL");
String auth= extras.getString("Authorization");
if (URL != null && auth!=null) {
webView.loadUrl(URL);
Map<String, String> headers = new HashMap<>();
headers.put("Authorization", auth);
WebViewClient wc= new myWebClient();
webView.setWebViewClient(wc);
webView.loadUrl(URL, headers);
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

18
Backend : Python Server
I want DEMO!
Python Webserver: The loaded webpage is expected to return a HTTP-302 redirect response.
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

19
Token leakage in header
Authorization header is sent to the redirected request as shown in Burpsuite (HTTPS Proxy)
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

20
Demo! Demo! Demo!
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

2222
Rollout Plan & Official Fix!
https://chromium.googlesource.com/chromium/src.git/+/6e46cca3ee484bac0cdb5d4bdae69a18857f8efd
Remove any extra headers from the request if the request is redirected to a different origin, since they might
be sensitive.
Record metrics on when we add headers and what was done with them on redirect.
Add an additional test verifying that the extra headers are cleared if the app loads the same URL
again via loadUrl(url).
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

23
Common
Webview Security
Issues

24
Common Webview Related Security Issues
Let’s understand some common webview related security issues
Lack of URL Validation
Insufficient URL Validation
Unintended Leakage of Sensitive Data to Third-parties
Insufficient Webview Isolation/Loading Untrusted Content
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni
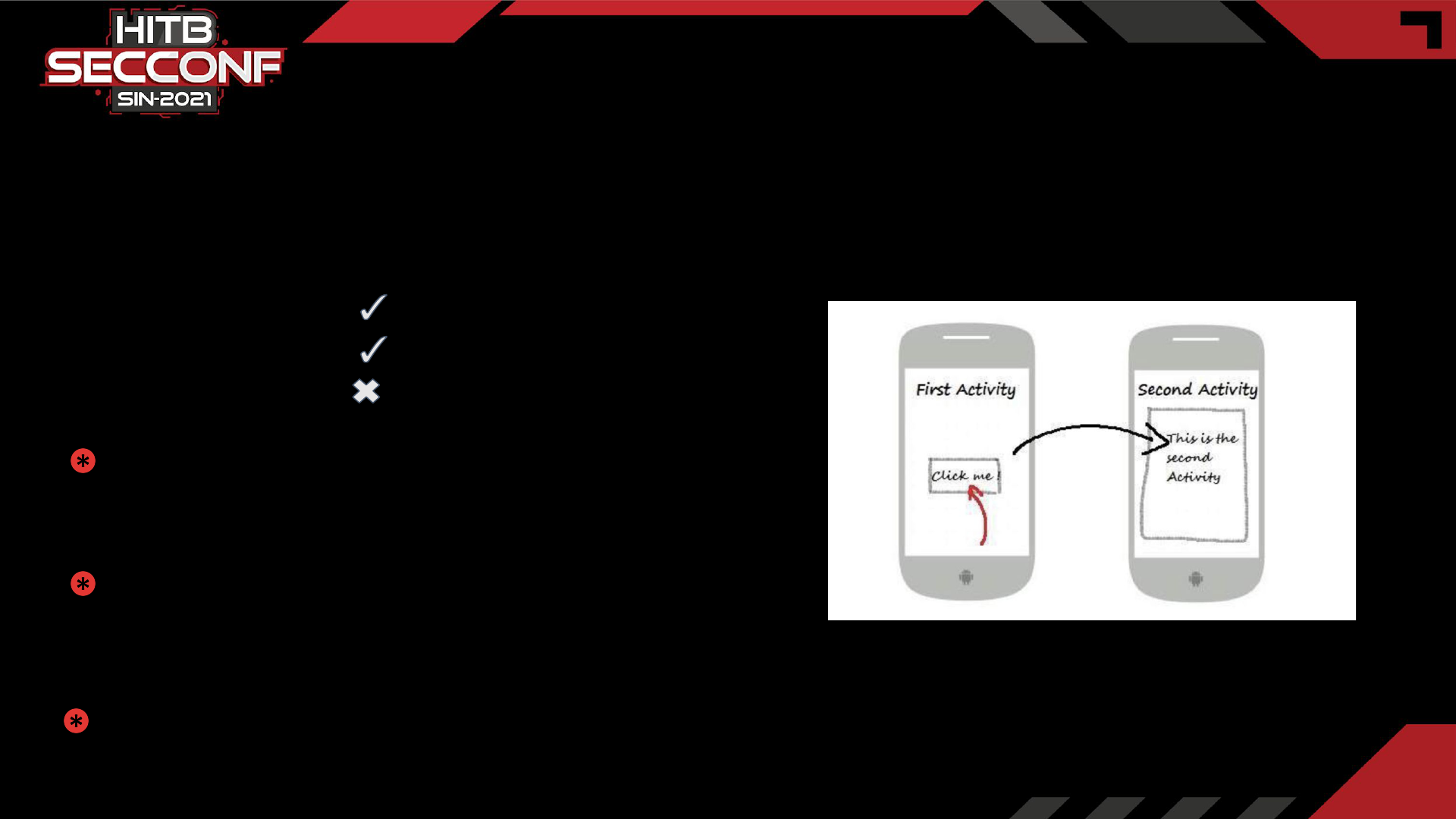
25
Triggering URL Load in Webviews
User Experience and Security Tradeoff
● Improved User Experience
● Code Reuse
● Security
Once Deeplink/Intent is triggered, it opens URL in the
webview component
Deeplink:
sampleapp://open?screenType=WEBVIEW&webviewUrl=
<urlToOpen>
Vanilla Intents:
am start -n <packageName>/.<componentName> --es
urlParam <urlToOpen>
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

26
Load of Arbitrary Web Content Due to
Misconfigured Webviews
AKA Insecure Deeplink Implementation-No URL Validation
For example if an application acknowledges the following deep link
webviewdemoapp://issue=1&url=https://scripts.shivsahni.com/testsample.html
//parse URL from deeplink
--
/*deeplinkURL=https://scripts.shivsahni.com/testsample.
html/*
--
webView.loadUrl(deeplinkURL);
--

28
Insufficient URL Validation
Insecure Deeplink Implementation-Insufficient URL Validation
For example if an application acknowledges the following deep link
webviewdemoapp://issue=1&url=https://scripts.shivsahni.com/testsample.html
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

29
Insufficient URL Validation-Example
Exploit! Exploit! Exploit!
Through the crafted URL in the Deeplink the validation could be bypassed resulting in arbitrary load of
malicious scripts
In the scenario wherein the webview is privileged(JS Bridges), it could even lead to exfiltration of auth
tokens
The issue was fixed in API level 28. However, API 27 and below are still vulnerable to such attacks
Read more here: Golden techniques to bypass host validations in Android apps by Bagipro
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

30
Escalating The Impact
From Insecure URL Validation to Exfiltration of User’s Auth Tokens
The Impact majorly depends on the privileges of the webview component under attack. The webview could
be having the following privileges:
Read more here: Golden techniques to bypass host validations in Android apps by Bagipro
Executing JavaScript
Access JavaScript Interfaces/Bridges( Allowing JavaScript to execute Native Code)
Access to other application components such as Content Providers, Local Storage, etc.
setAllowUniversalAccessFromFileURLs: Sets whether cross-origin requests in the
context of a file scheme URL should be allowed to access content from any origin
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

31
Unintended Data Leakage
How we could be sharing user’s PII/sensitive information to third-parties unintentionally
Authenticated load to third-party domains
Authenticated load with JWT in query string
Leakage of JWT in Referer header

32
Leaking Token in Referer Header
Unintended Data Leakage
GET /gtm.js?id=GTM-TSGF649 HTTP/1.1
Host: www.googletagmanager.com
Referrer:
https://myapp.com/?id_token={id_token}
Accept-Language: en-us
Accept-Encoding: gzip, deflate
Connection: Keep-Alive
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

33
Authenticated Loads to Third-Party Domains
Unintended Data Leakage
GET /oauth2/authorize HTTP/1.1
Host: www.third-party.com
Authorization: {JWT}
Accept-Language: en-us
Accept-Encoding: gzip, deflate
Connection: close
HTTP/1.1 302 Found
Date: Fri, 27 Aug 2021 09:44:33
GMT
Content-Type: text/html;
charset=utf-8
Content-Length: 50
Connection: close
Location:
https://third-party.com/init/sta
rt
Auth Token exposed to
third-party
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

34
Authenticated Loads with JWT in Query String
Unintended Data Leakage
GET /?authToken={token} HTTP/1.1
Host: myapp.com
Accept-Language: en-us
Accept-Encoding: gzip, deflate
Connection: close
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

35
Lack of Webview Isolation
An introduction to Custom Chrome Tabs and Safari View Controller
Are you loading third-party websites in the webview instance
of your application?
Is that webview instance privileged? JavaScript Enabled/JS
Bridges?
What happens if there is breach of trust or the third-party is
compromised?
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

36
Learnings &
Recommendations

37
Secure URL Validation
Let’s Secure Android Webviews!
For example if an application acknowledges the following deep link
webviewdemoapp://issue=1&url=https://scripts.shivsahni.com/testsample.html
private fun validateURL(urlString: String):Boolean
{
try {
URL urlObject= new URL(urlString);
if((urlObject.getAuthority()=="shivsahni.com")&&(urlObject.getSc
heme()=="https"))
return true;
}
catch (MalformedURLException e)
{
e.printStackTrace();
return false;
}
}
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

38
Secure URL Validation
Let’s Secure iOS Webviews!
It is highly recommended to check a URL against a whitelisted domain and explicitly match with
urlComponents.scheme, urlComponents.host
//Swift code
func validateURL(url: URL) -> Bool {
guard let urlComponents = URLComponents(url: self,
resolvingAgainstBaseURL: false),
urlComponents.scheme == "https://" &&
urlComponents.host == "myapp.com" else {
return false
}
return true
}
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

39
Webview Isolation
An introduction to Custom Chrome Tabs and Safari View Controller
Chrome Custom Tabs and Safari View Controllers are what we recommend when browsing 3rd party sites,
as the loaded web content is being executed under the chrome process, it minimizes the risk of malicious
javascript accessing application’s non-exported services.
Chrome Custom Tabs and Safari View Controller will embed the browser into the native app, to make
transitions between native and web content more seamless without having to resort to a WebView.
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

40
Defence in Depth
Let’s harden Android webviews!
Disable implicit access to Content Providers: setAllowContentAccess()
Disable implicit access to Local Storage: setAllowFileAccess()
Reduce sensitive data exposure by flushing webview cache whenever webview component is no
longer required: clearCache()
Ensure that the JS is not unnecessarily enabled, in case the JS execution is required make sure that it
is coming from trusted source over a secure channel: setJavaScriptEnabled()
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

41
Defence in Depth: Risk of using UIWebView?
Let’s harden iOS webviews!
UIWebView is deprecated on iOS 12. The App Store does not accept new apps or updated to existing
apps that use UIWebView. https://developer.apple.com/news/?id=edwud51q
Security-sensitive settings are enabled by default
Javascript cannot be disabled.

42
Defence in Depth: Why use WKWebview?
Let’s harden iOS webviews!
Although JavaScript is enabled by default, it can be disabled using javaScriptEnabled property.
The hashOnlySecureContent property can be used to verify resources loaded by the WebView are retrieved
through encrypted connections.
While using allowingReadAccessToURL do not give access to local storage directory rather specify the file
to be accessed by webview.
Security-sensitive settings such as allowFileAccessFromFileURLs & allowUniversalAccessFromFileURLs
are disabled by default
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

43
Follow the principle of least privileges while configuring
webviews. For example, only enable JS if explicitly required.
Use Chrome Custom Tabs/Safari View Controllers wherever
possible to load untrusted content(third-party web content, etc.)
If your webview is programmed to load the URL in deeplink
ensure the URL is validated before the load
While validating the URL before loading in the webview,
explicitly match against URL authority and protocol
While doing a third-party integration make sure no sensitive
user information is shared unintentionally.
KEY
TAKEAWAYS
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

44
Honorable Contributors
Movnavinothan V and Changmook Lim for helping us during the analysis to come up
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

45
References
Carnegie Mellon University-Webview Secure Coding Practices
Leakage of Sensitive Data Through Android Webviews
OWASP Mobile Security Testing Guide
Bypassing Webview Host Validation-Bagipro
Unintended Data Leakage Through HTTP Request Headers
Building Safe URL in Swift
Securing Webviews & The Story Behind CVE 2021-21136 | Imdadullah Mohammed & Shiv Sahni

Thank You for Joining
Us
Join our Discord channel to discuss more or ask questions
https://discord.gg/dXE8ZMvU9J




